Using Digital Scaffolding to Build Your Child’s Human Firewall 🏗️🛡️
Stop the "Amygdala Hijack." A pragmatic incident response plan for parents navigating the emotional punch of the digital world. Featuring the S.H.I.E.L.D. protocol and the ANT-Eater method.

Building a "fortress" around our children with apps and filters feels safe, but I’ve learned that eventually, a message always slips through. In the age of AI-generated deepfakes and algorithmic "hooks," I cannot just block the world; I have to build a Human Firewall inside my children so they can process digital toxicity without it breaking their spirit.
This isn’t just about safety; it’s about resilience. While I use the Admin Console to manage our data, the Human Firewall is the internal capability that prevents Social Engineering—the psychological manipulation of our kids—from succeeding.
Part 1: The "Why" (Understanding the Digital Sting)
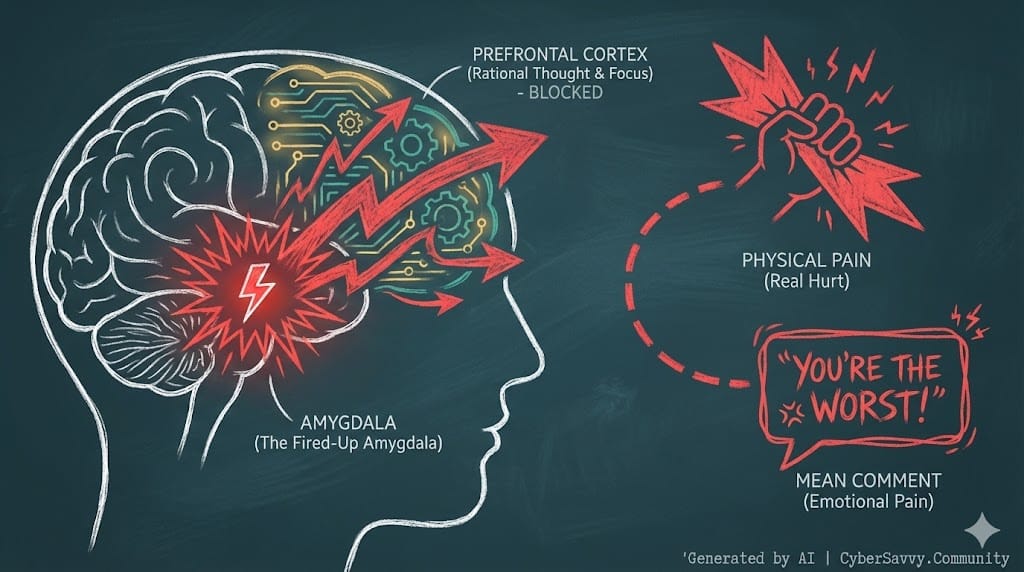
When my child sees a hostile comment or a fake image, it isn't "just words." Science shows that digital rejection—like being excluded from a group chat—activates the same regions of the brain that process physical pain.
Their "threat detector"—the amygdala—takes over, flooding the body with stress and bypassing their rational logic center. This is an "Amygdala Hijack," and it renders a child physiologically incapable of "just ignoring it" without external help.
Part 2: What to Do in the Heat of the Moment
When the brain gets stuck in a stress loop, use these protocols to re-engage the logic center.
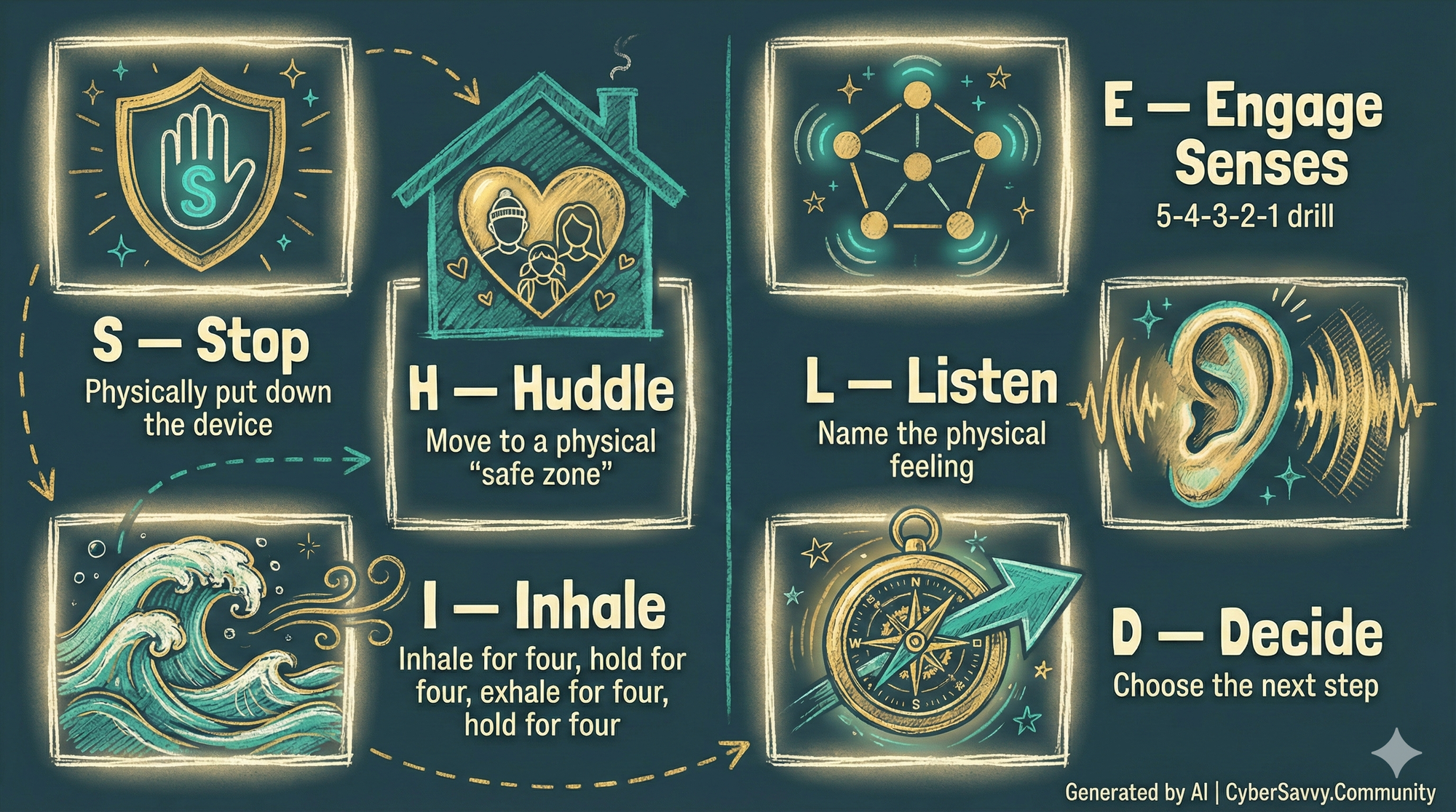
The S.H.I.E.L.D. Pause
Physically put down the device immediately; do not type back.
Move to a physical "safe zone" in the house to break the digital immersion.
We do "Square Breathing" : Inhale 4, Hold 4, Exhale 4, Pause 4) - to tell the brain it is safe.
We perform the "5-4-3-2-1" drill to pull the brain back to the real world.
- 5 - Acknowledge five things you see around you. This could be a picture on the wall, a crack in the pavement, a cloud, or anything else in your visual field.
- 4 - Acknowledge four things you can touch or feel. Focus on the sensation, such as the texture of your clothing, the smooth surface of a table, the warmth of a cup, or the ground under your feet.
- 3 - Acknowledge three things you can hear. Pay close attention to sounds you might usually filter out, like the hum of a refrigerator, distant traffic, or the ticking of a clock.
- 2 - Acknowledge two things you can smell. Note the scents in your environment, such as coffee brewing, soap, or fresh air.
- 1 - Acknowledge one thing you can taste. If possible, actively taste something (like a sip of water or a piece of gum). If not, simply notice the current taste in your mouth.
I ask them to name the physical feeling, like a tight stomach or a hot face.
Only when the physical "heat" subsides do we choose the next step.
Capture, Don’t Comment (The Logic Layer)
Once calm, I shift my child from "victim" to "investigator." We take screenshots and evidence for our Crisis protocol.
If it involves a suspicious image, we go "Hallucination Hunting" for glitches like extra fingers or weird shadows. I use a local, offline installation of GIMP (it can perform Level Analysis and Error Level Analysis (ELA) manually to spot inconsistencies in an image's compression). Once done, we label it for what it is: Synthetic Slop.
The ANT-Eater Method (Protecting Self-Esteem)
Bullying causes ANTs (Automatic Negative Thoughts).
- Catch it: Identify the thought (for example: "Everyone hates me").
- Check it: Is it "everyone," or just two people? Is it fact or opinion?
- Change it: Replace it with a fact: "Two people were mean online, but my friends at soccer still like me. I am safe offline."
Proactive "Sparring" (Preparing Before the Fight)
Resilience is a learned competency built through "emotional flight simulators."
- Digital Vitamin C: We use tools like Spoofy or Interland to practice blocking bullies and reporting toxic behavior in a safe environment.
- Role-Exchange Scenarios: We act out situations where they play the victim, then the bully, then the Upstander.
- The Magic Key Defense: We practice refusal scripts for apps asking for voice or face data: "My voice is my Magic Key. I don't share it."
My Promise (The Parent's Role)
I’ve learned that children will not report bullying if they fear their device will be taken away. To be their "biological buffer," I follow these rules:
- The Contract: I tell them: "If you come to me with a problem online, my first job is to help you, not to punish you or take your device."
- Loud Thinking: I narrate my own digital regulation. If an email makes me angry, I say: "Wow, I’m frustrated. I’m putting my phone down to breathe before I decide how to reply."
- Circle of Trust: We physically map out "Safe Adults" they can go to without fear of judgment.
- Stay Calm: If they disclose a problem, I stay calm. If I panic, I only reinforce their fear.
By shifting from surveillance to mentorship, I am graduating my children from being passive users to empowered Cyber-Savvy Pilots.